The Most Common Cyberattacks and How to Protect Yourself

Digital threats are always innovating and evolving. Understanding the most common types of cyberattacks and how to defend against them is crucial for individuals and organizations. Here are some of the most common threats and some suggestions on how to stay protected.
Email Phishing Attacks
Email Phishing remains one of the most prevalent and dangerous cyber threats. Attackers use deceptive emails, websites, or messages to trick victims into revealing sensitive information or clicking on malicious links.

How to Protect Yourself from Phishing Attacks
- Be skeptical of unsolicited emails, especially those requesting personal information.
- Verify the sender's email address and look for signs of impersonation.
- Hover over links before clicking to check their true destination.
- Use multi-factor authentication (MFA) on all important accounts.
- Keep your software and systems updated to patch known vulnerabilities.
- Emails that require immediate attention or create a sense of urgency should be reviewed carefully as attackers use those methods to trick you into clicking links.
Malware
Malware, including viruses, trojans, and ransomware, can infect your devices and compromise your data and privacy.

How to Protect Yourself from Malware Attacks
- Install and regularly update reputable antivirus software.
- Be cautious when downloading files or clicking on links from unknown sources.
- Back up your data regularly to a separate service or cloud location to protect against ransomware attacks.
- Use a firewall to monitor and control incoming and outgoing network traffic.
Password Attacks
Cybercriminals often attempt to gain unauthorized access to accounts by guessing or cracking passwords.

How to Protect Yourself from Password Attacks
- Use strong, unique passwords for each account. Passwords or passphrases with more than 16 characters and complex are the best option.
- Implement a password manager to generate and store complex passwords securely.
- Enable MFA wherever possible.
- Avoid using easily guessable information in your passwords, such as birthdays or common words.
Man-in-the-Middle (MitM) Attacks
In MitM attacks, attackers intercept communication between two parties to eavesdrop or manipulate the data being exchanged.
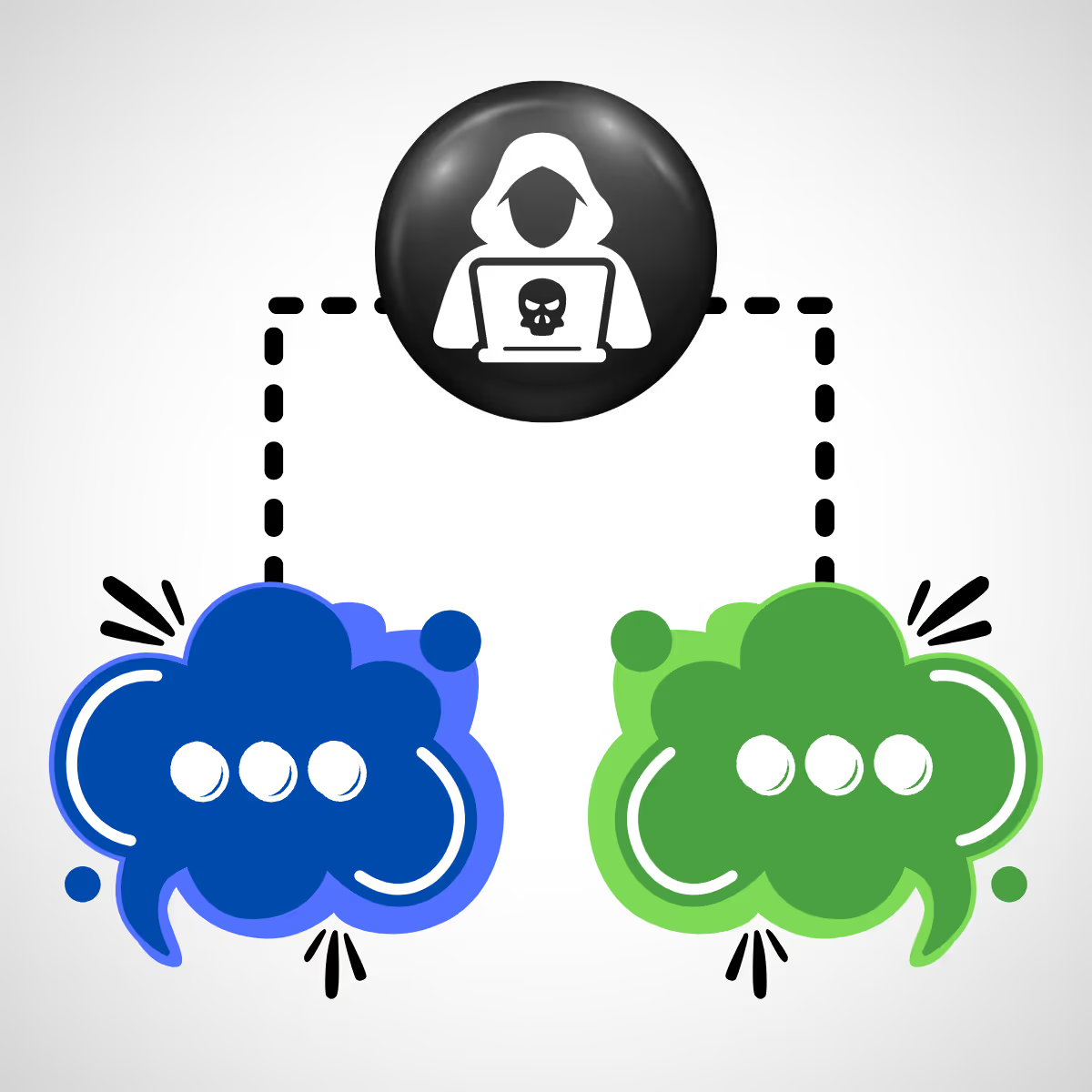
How to Protect Yourself from MitM Attacks
- Use a Virtual Private Network (VPN) when connecting to public Wi-Fi networks.
- Ensure websites you visit use HTTPS encryption (look for the padlock icon in the address bar).
- Avoid conducting sensitive transactions on public Wi-Fi networks.
- Keep your home Wi-Fi network secure with a strong password and WPA3 encryption.
- If possible use a segregated guest network at your home to reduce the risk of unknown devices connecting to your network.
- If possible use a segregated device network for IOT devices.
Social Engineering
Social engineering attacks exploit human psychology to manipulate victims into divulging confidential information or performing actions that compromise security.

How to Protect Yourself from Social Engineering Attacks
- Be wary of unsolicited phone calls or messages asking for sensitive information.
- Verify the identity of individuals requesting access to secure areas or systems.
- Educate yourself and others about common social engineering tactics.
- Implement strict policies and procedures for handling sensitive information.
Distributed Denial of Service (DDoS) Attacks
DDoS attacks overwhelm a target system or network with a flood of traffic, rendering it inaccessible to legitimate users.
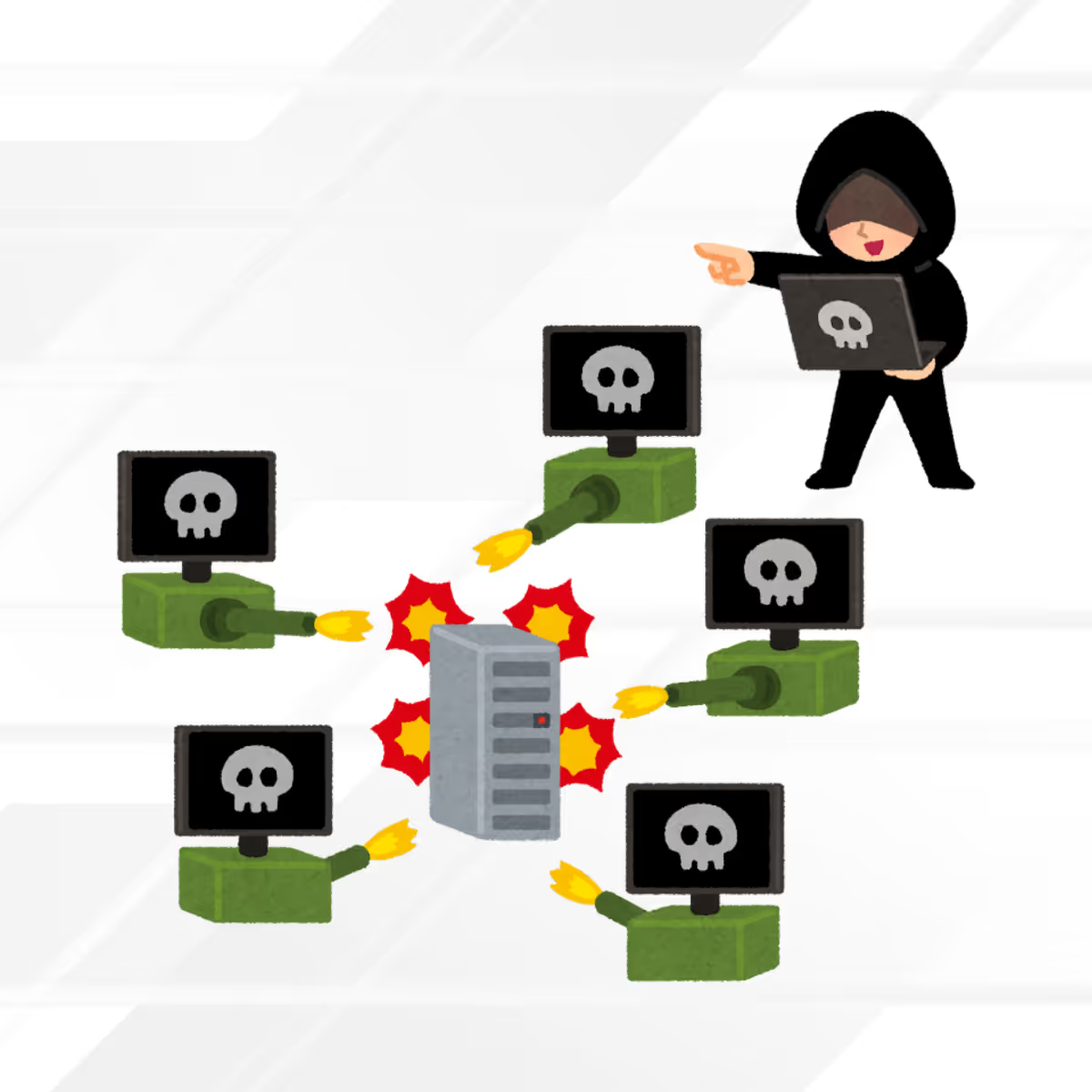
How to Protect Yourself from DDoS Attacks
- Use a reputable DDoS mitigation service or content delivery network (CDN).
- Regularly monitor your network for unusual traffic patterns.
- Develop and maintain an incident response plan.
- Keep your systems and software up to date to patch known vulnerabilities.
By understanding these common threats and implementing the suggested protective measures, you can significantly reduce your risk of falling victim to a cyberattack. Remember, cybersecurity is an ongoing process, and staying informed about emerging threats is key to maintaining a strong defense.
Let's Talk!
[gravityform id="2" title="false" description="false" ajax="false" /]
Keep Your Business Running with 24/7 IT Support.
Get reliability, security, and peace of mind from a partner that picks up every time. Fill out a quick form and get in touch with us today!


.jpg)
